Neat Tips About How To Prevent Arp Spoofing
It’s possible to statically map all the mac addresses in a network to their rightful ip addresses.
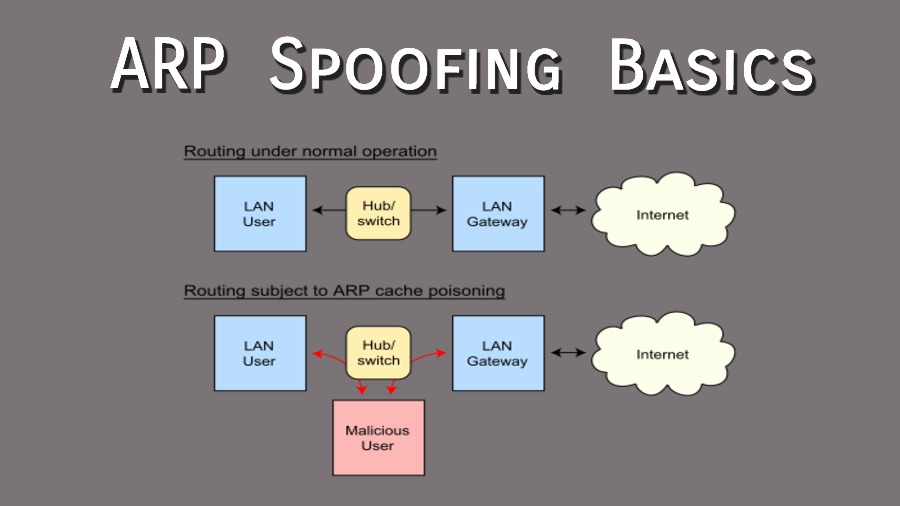
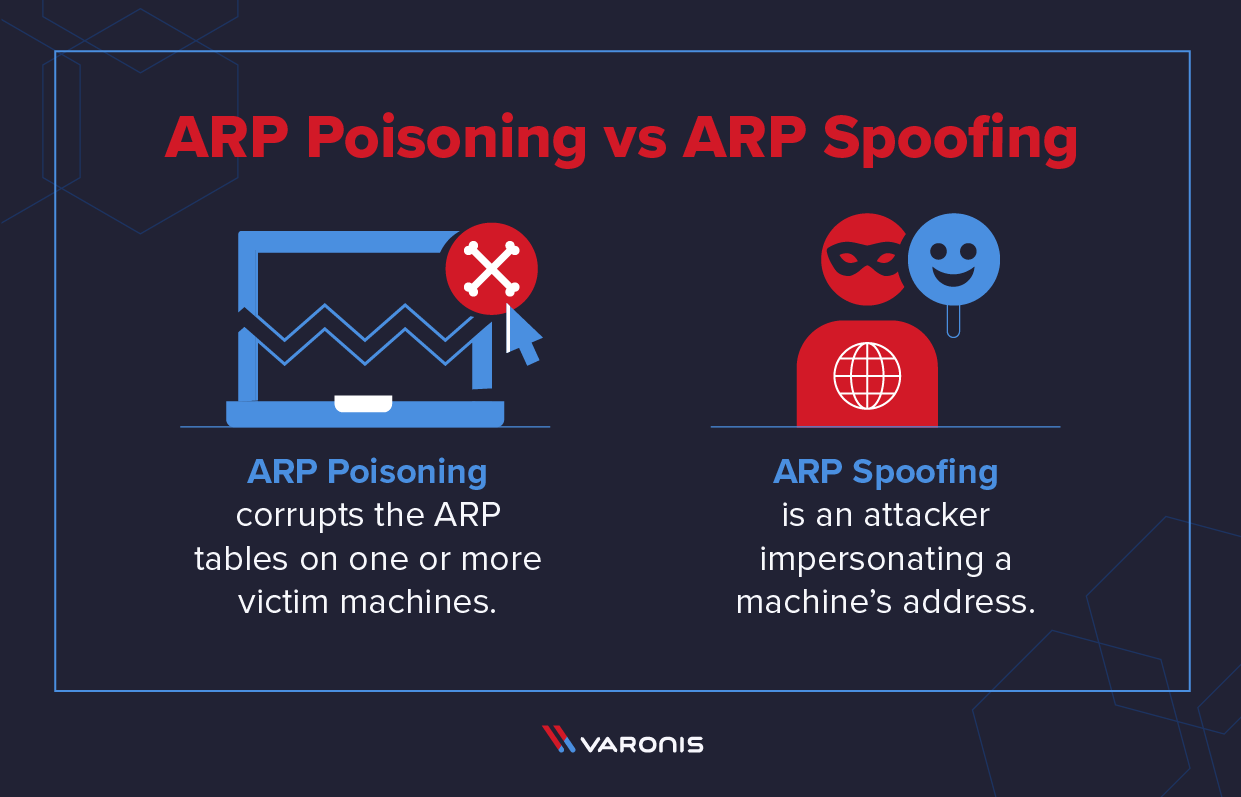
How to prevent arp spoofing. As krytical mentioned, setup arpwatch and then capture. Finally, after going through the rest of the items on. How to prevent arp poisoning attacks static arp tables.
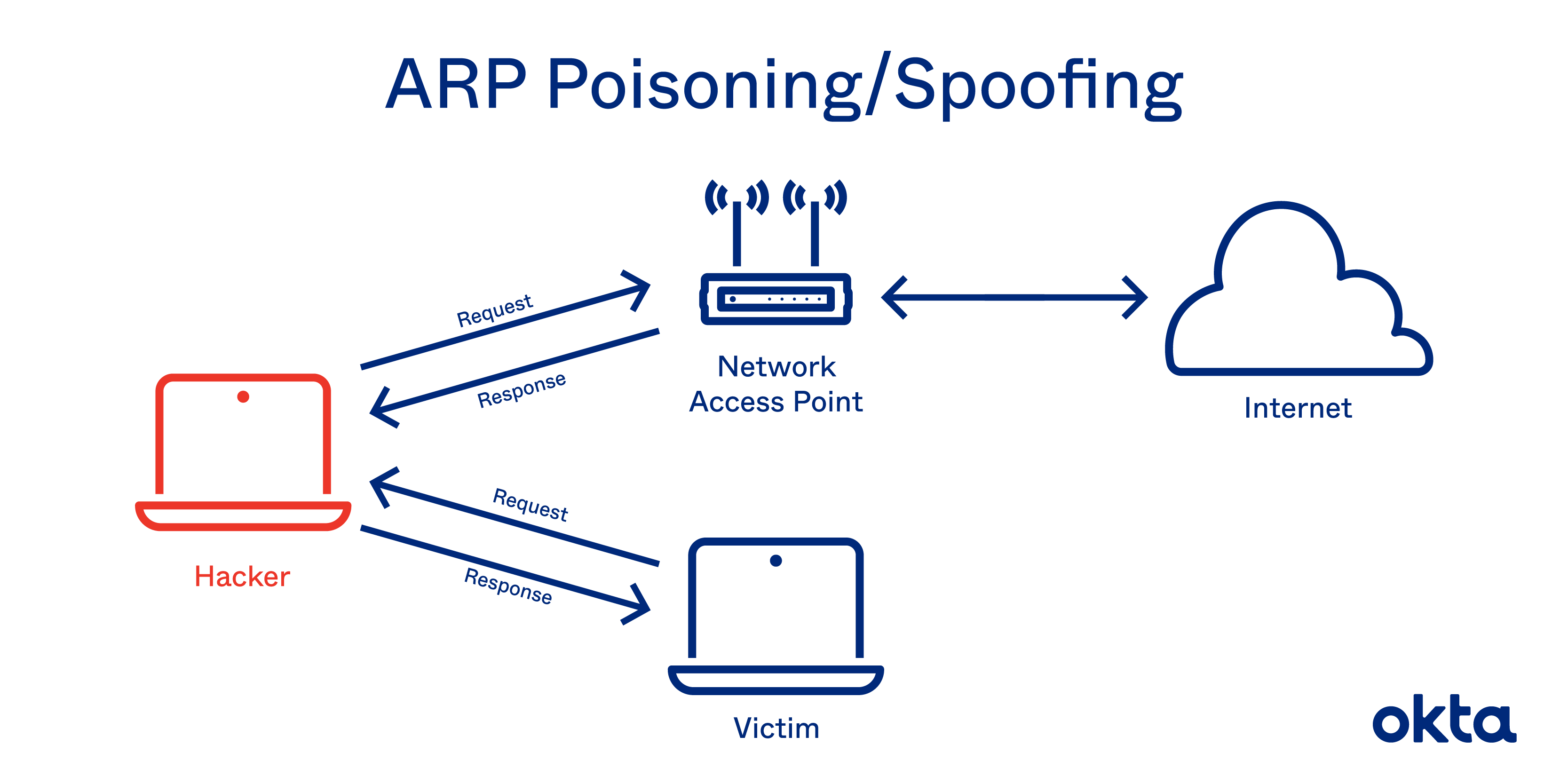
Tools for preventing arp spoofing. Firstly, it is important to ensure that all devices on the network have unique. Besides using an arp spoofing detection software (or command), what else can you do to prevent such attacks?.
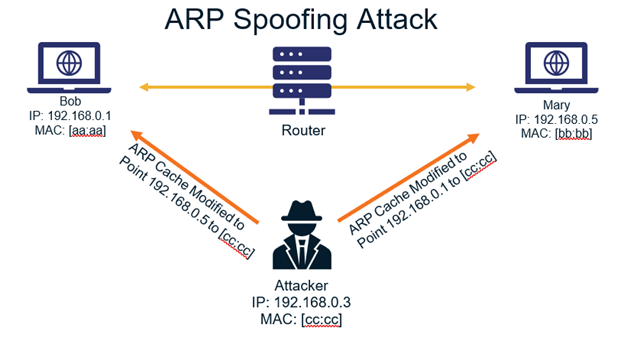
Mapping the devices with sets of static ip and mac addresses serves to block spoofing attacks because the devices can neglect arp replies. One obvious one is to invest in some detection software that will allow you to spot potential threats. This will cause intermittent communications issues.
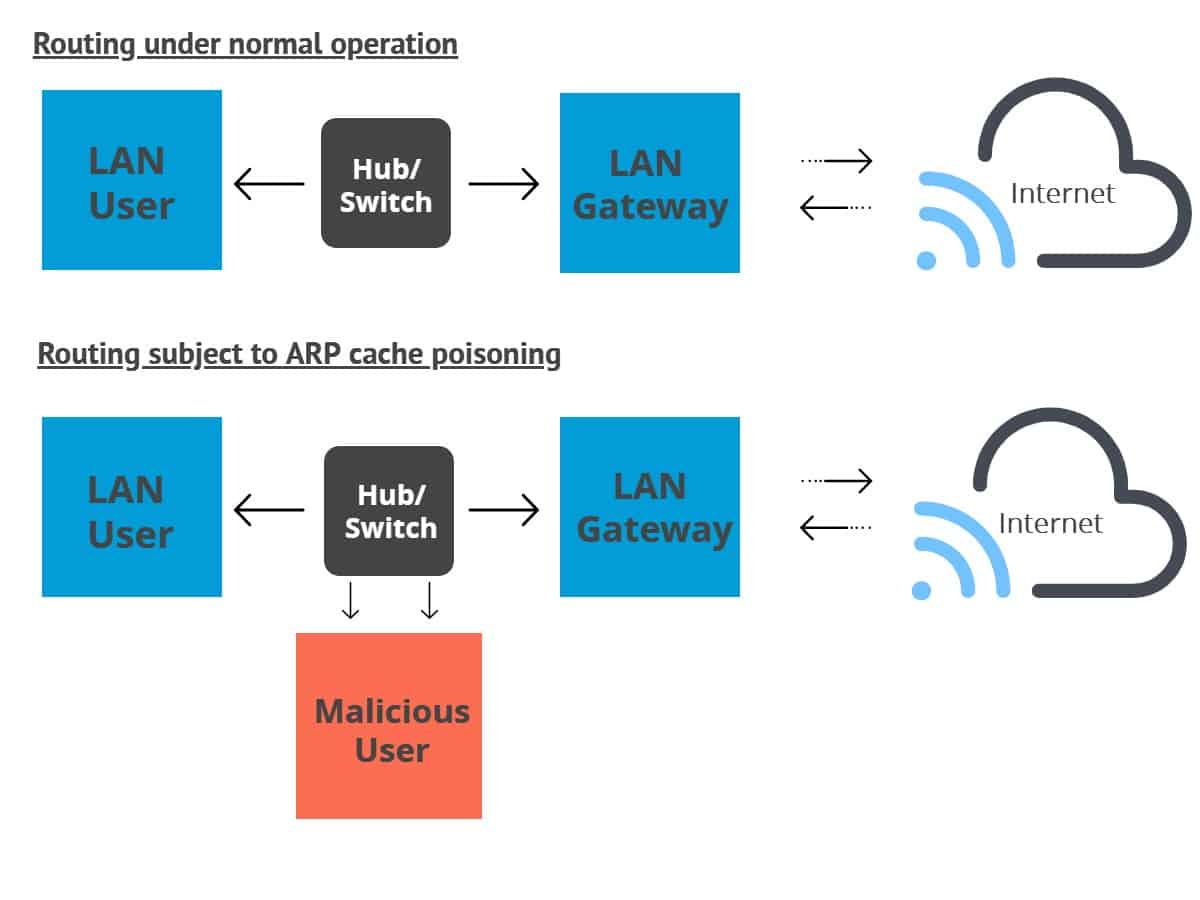
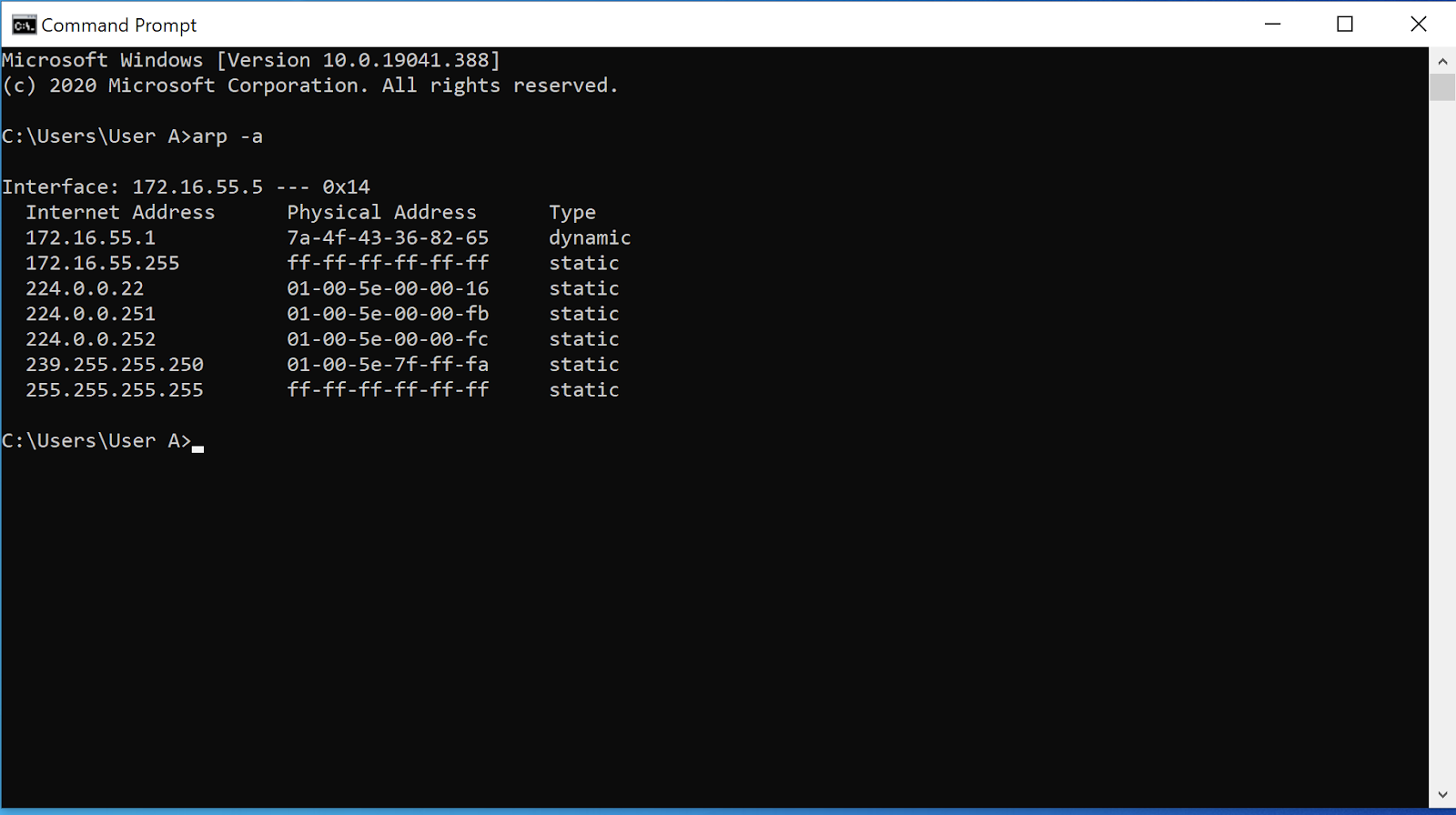
What it is doing for you now is responding for devices attached to your lan. Encryption is one of the best ways to protect yourself from arp spoofing. There are several ways you can prevent arp spoofing attacks.
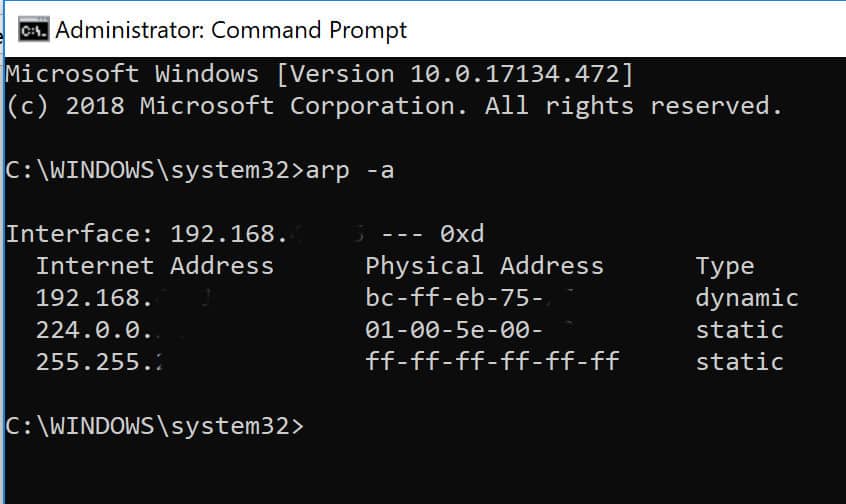
3.use xarp software for monitoring your arp table. How to prevent arp spoofing? How to prevent arp spoofing (and protect your ip address and mac address)?
Xarp is a freeware software that automatically scans your arp table, and if it spoots a duplicate mac address, it is alerting. There are a number of measures that can be taken in order to prevent arp spoofing attacks.